The rapid move to hybrid work brought about by the pandemic drove the adoption of Zero Trust Network Access (ZTNA) as a way to securely connect users with the applications that they need to get work done from anywhere. However, as I described in my first article, initial implementations of ZTNA have been deeply flawed.
In my previous post, I talked about how the ZTNA 1.0 concept of “allow and ignore” is a recipe for disaster. This concept maintains that once a connection is established, all user and device behavior for that session is trusted implicitly and goes unchecked. Unfortunately, another limitation of the “allow and ignore” approach is that it prohibits security inspection of the traffic.
ZTNA 1.0 Lacks Security Inspection
Because the “allow and ignore” model lacks security inspection, there is no means for a ZTNA 1 .0 solution to detect any malicious or other compromised traffic and respond accordingly. This means there are no in-line controls to expose and inspect the traffic payload and determine if anything malicious or unknown is being introduced. Likewise, there is no mechanism to take action by blocking traffic, terminating the session, or reporting anything unusual, at the very least.
This turns ZTNA 1.0 into a “security-through-obscurity-only” approach, which further puts organizations, their users, apps, and data at risk of malware, compromised devices, and malicious traffic.
ZTNA 2.0 Enables Continuous Security Inspection
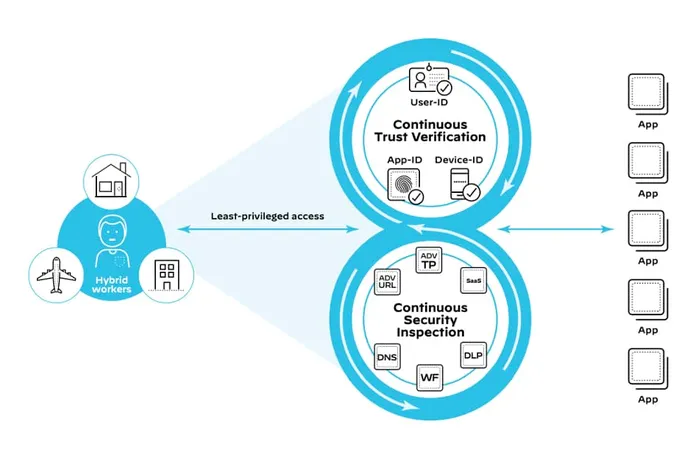
ZTNA 2.0, delivered by Prisma Access, provides deep and ongoing inspection of all traffic, to prevent all threats, including zero-day threats. This is especially important in scenarios where legitimate user credentials have been stolen and used to launch attacks against applications or infrastructure. ZTNA 2.0 offers complete protections that safeguard against even the most sophisticated threats, including WildFire sandboxing, Advanced URL Filtering, threat pPrevention, SaaS security, DNS security, and more.
Our AI and ML-powered threat prevention technologies stop 95% of zero-day threats inline. This means you don’t need a first victim or have to wait for signatures to be updated to be protected – your environment is instantly protected.
The combination of continuous trust verification and continuous security inspection is a powerful model for delivering better security for today’s hybrid workforces and overcoming some of the shortcomings of ZTNA 1.0 solutions.
ZTNA 2.0 Is Zero Trust with Zero Exceptions
The shift to a dynamic, hybrid workforce combined with direct-to-app access has dramatically increased the attack surface. Pursuing a true Zero Trust posture is the best way to defend this new reality, and ensuring that security inspection is conducted in a robust and consistent manner is an important step. That’s why continuous security inspection is an important component of ZTNA 2.0.
Be sure to watch our ZTNA 2.0 virtual event, where we discuss innovations and best practices for securing the hybrid workforce with ZTNA 2.0.

Kumar Ramachandran serves as Senior Vice President of Products for Secure Access Service Edge (SASE) products at Palo Alto Networks. Kumar co-founded CloudGenix in March 2013 and was its CEO, establishing the SD-WAN category. Prior to founding CloudGenix, Kumar held leadership roles in Product Management and Marketing for the multi-billion dollar branch routing and WAN optimization businesses at Cisco. Prior to Cisco, he managed applications and infrastructure for companies such as Citibank and Providian Financial. Kumar holds an MBA from UC Berkeley Haas School of Business and a Master's in Computer Science from the University of Bombay.
